Qcells Cybersecurity
Cybersecurity Approach
Qcells adopts a cybersecurity framework that is based on Hanwha’s corporate policy and is implemented down to each of our business units. This means that each division considers core aspects of cybersecurity as a part of our program. Qcells routinely goes through security and risk assessments at various cadences for our products (web, phone, cloud, device) with Hanwha, which includes tasks such as:
- Security inspection and vulnerability assessments
- Penetration testing (internal and external)
- Critical vulnerabilities and response
- System audits
The security framework is based on the Cybersecurity and Infrastructure Security Agency Cross-Sector Cybersecurity Performance Goals (CISA CPG), which itself is modeled after the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF).
The Qcells cybersecurity program covers relevant firmware and software, including our battery storage and renewable energy systems, for residential, commercial, and utility-scale applications. Qcells is also committed to implementing robust data privacy measures and adheres to local and international laws, including the California Consumer Privacy Act (CCPA), California Privacy Rights Act (CPRA), and other regulations in jurisdictions where Qcells products are deployed.
Device Security
Qcells supplies various edge devices and protects hardware like computers, mobile devices, and IoT devices (e.g., endpoint protection, antivirus). Qcells hardware (i.e. node and energy management system) have built-in firewalls.
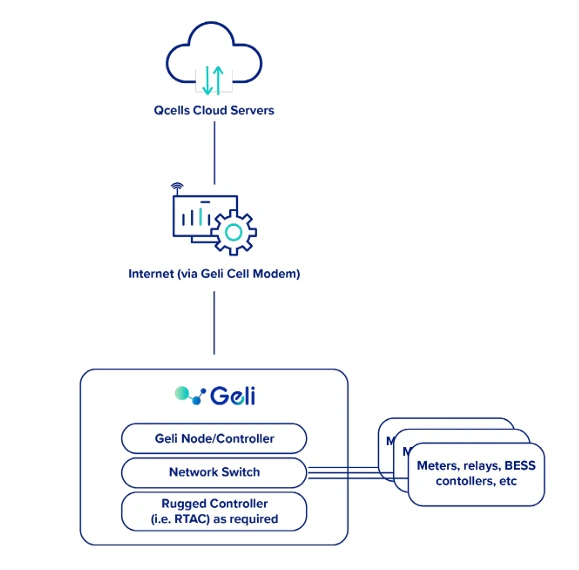
C&I (Node): EOS Node and Current Cloud Architecture
The Qcells energy operating system Node is a Linux-based controller that Qcells utilizes for connectivity to on-site battery storage and microgrid hardware and is used for optimization, controls, and connectivity to our cloud systems for system monitoring.
Authorized Qcells personnel can connect directly to a Qcells system to run diagnostics using multi-factor authentication (MFA) with defined role-based access levels. The customer can both monitor their system via the Insight application which also has MFA and role-based access control. Customers are responsible for implementing and maintaining additional security measures beyond those provided by Qcells. Local communication between the Qcells controller and inverter/batter energy storage system (BESS) blocks is on the internal Ethernet network over a private transmission control protocol (TCP) network.
*For detailed information on customer responsibilities, limitations of liability, and other terms, please refer to the applicable Qcells customer agreement.
Communication between the on-site node and remote systems/servers is through mTLS using X.509 certificates.
Qcells controls components come in a lockable cabinet or enclosure that is located near the battery energy storage system (BESS)/photovoltaic (PV) system for physical security measures.
Indicative Diagram
Residential
In addition to the C&I space, Qcells also offers residential products such as Q.HOME, Q.OMMAND, and AC systems that are utilized by individual homeowners, Qcells partners, and installers that must also adhere to device and software cybersecurity requirements and standards. The Qcells residential offering includes device security for the local equipment and components, cloud security for Over-The-Air updates and monitoring, and mobile security for installer and home apps.
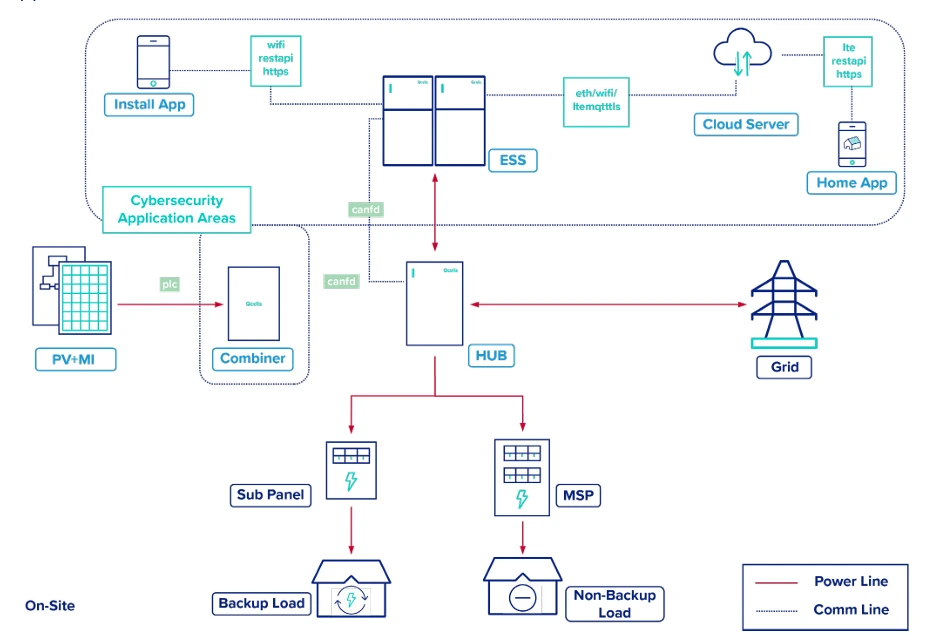
Qcells endeavors to maintain up-to-date software versions through regular updates, subject to applicable operating conditions and customer cooperation. Updates are conducted via methods to distribute the load on servers. These updates are staggered according to the serial number of each device and are executed at predetermined times.
Our update functionality includes two methods: targeting devices for updates via the web and updating at scheduled times. The general deployment method to ensure the latest software version is maintained uses the scheduled update approach, while the targeted update method is employed for maintenance and management purposes. Also, Qcells residential battery products are UL5500 certified for remote software updates. In addition to OTA methods, Q.HOME updates are available only to authorized people like installers or customer support.
Software Development Security
Qcells goes through a secure software development lifecycle (SDLC), which focuses on securing applications (e.g., patch management, secure coding, vulnerability scanning). Qcells software development security includes processes such as:
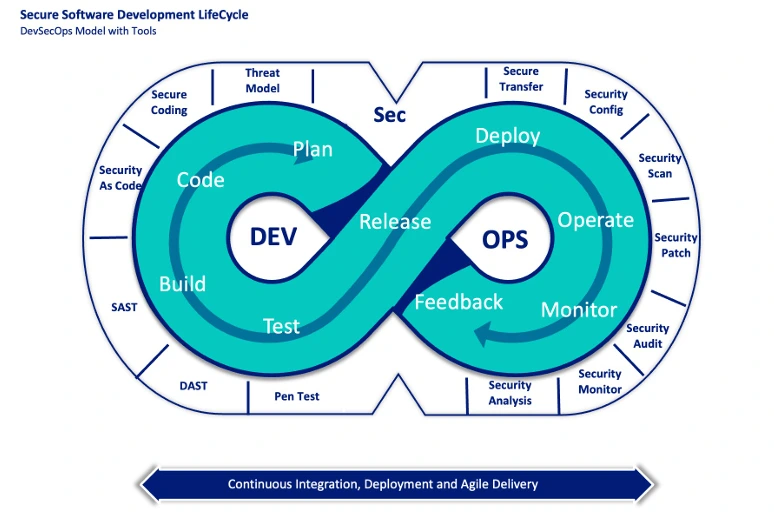
- Planning/design and development: Development team ensures that there are advanced security reviews, and the system is only released after inspection.
- Testing: Includes static security check, vulnerability check, and cloud console security check (if applicable).
- Distributing: Only after vulnerability measures are completed and reviewed/remediated.
- Operations: Includes regular vulnerability checks and cloud console security checks (if applicable).
In the event of critical system errors or vulnerabilities, we implement an expedited hotfix deployment process. This involves rapidly identifying the issue, developing and testing the fix, and deploying it to the affected components with minimal downtime. Hotfixes are distributed via a rolling update mechanism, ensuring that the system remains operational and stable throughout the process. We also conduct rigorous testing in staging environments that mirror the production setup to validate the updates before deployment. This ensures that both regular updates and hotfixes maintain the integrity and performance of the system.
Network Security
Qcells residential and C&I solutions require various levels of network security to prevent unwanted access and to ensure customer systems remain secure. Some of the safeguards that Qcells deploys may include network infrastructure such as firewalls and intrusion detection/ prevention systems for our C&I systems. Both our commercial and residential products incorporate whitelisting to prevent unwanted access.
Cloud Security
For cloud security, Qcells uses built-in tools to help monitor and prevent unwanted access to protect data and applications in cloud environments (e.g., encryption, identity management). This is accomplished by:
- Implementing a least privileged approach and a zero-trust architecture
- Removing access to terminated employees promptly upon separation
Qcells adheres to Institute of Electrical and Electronics Engineers (IEEE) 2030.5 certification for cloud telemetry aggregation (VPP, IMS inverter management service).
Process/Policy Security
As noted, Qcells follows the CISA CPG which follows the NIST CSF and includes the various functions:
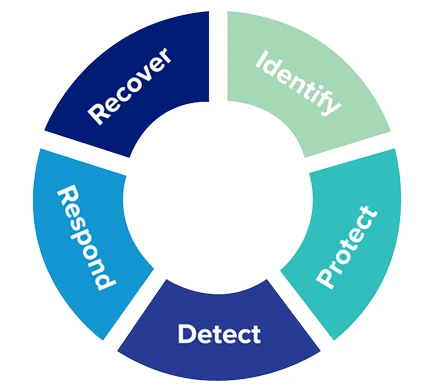
- Identify: Qcells applies principles of identifying vulnerabilities and includes vulnerability scanning and reducing the attack surface of adversaries by decreasing the likelihood of exploitation of networks and systems.
- Protect: For Qcells local and cloud systems, there are requirements around ensuring:
- Password complexity, changing default passwords
- Revoking access and accounts for departed employees
- Segmenting networks with VPN and firewalls
- Phishing resistant multi-factor authentication (MFA)
- Secure log collection and storage
- Up-to-date incident response plans
- Limiting connections to the public internet
- Detect: Includes end user antivirus and intrusion prevention and antivirus for cloud systems.
- Respond: Reporting incidents, vulnerabilities. Sharing findings.
- Recover: Business continuity and disaster recovery (including backups).
Data Security
Protects sensitive data through encryption, backups, and data masking. Qcells follow some of the most stringent privacy laws in the world including those of CCPA and CPRA.
Identity and Access Management
For access to any Qcells data or products, Qcells employs a least privilege approach and requires MFA for accessing systems and data, including strong password policies.
Qcells uses built-in identity and access management (IAM) for both Azure and Amazon Web Services (AWS).
- For Azure, we use Entra-ID.
- Entra ID identity management leverages capabilities which raises the security posture for users and application clients. Additionally, application programmer interface (API) management and protection of API endpoints is done through throttling and client credentials, which uses short-lived tokens.
- For AWS, we use Cognito.
- Cognito is a secure identity management service for user authentication and access.
*While Qcells implements advanced cybersecurity measures to protect its systems and products, no system can guarantee absolute security. Qcells’ liability for any damages resulting from cybersecurity incidents is limited as outlined in applicable customer agreements.
**All firmware, software, and other proprietary elements provided as part of Qcells products remain the intellectual property of Qcells or its licensors. Unauthorized duplication or modification is prohibited.
 USA & Canada
USA & Canada Korea
Korea Germany
Germany United Kingdom
United Kingdom France
France Italy
Italy Netherlands
Netherlands Greece
Greece Poland
Poland Portugal
Portugal Hungary
Hungary Spain
Spain Japan
Japan